Business Security Tool
What BST does
By following the Attribute-Based Access Control (ABAC) paradigm, our BST tool is capable of modelling, managing and providing an auditable presentation of business security policies for the applications of any organisation, company or institution.
BST is an authorisation engine which will help you administer your organisation's privileges efficiently, securely, and with complete customisation. All with uniform, centralised and auditable implementation and administration.
- Fine-grained control in real time.
- Zero Trust: Two-level security.
- Versatile and modular to adapt to business needs
- Centralised and efficient implementation and administration.
- Can be integrated with third-party applications.
- Possibility of creating customised connectors.
- Capacity to audit authorisation events.
- Can be integrated with IAM using the SCIM 2.0 protocol.
How BST does it
ABAC engine
The methods traditionally applied for access control do not fulfil the requirements imposed by the challenges of the extended company, nor can they efficiently secure access control to confidential information, in fulfilment of regulatory data access requirements.
For all these reasons, BST is based on Attribute-Based Access Control (ABAC). Attribute-based access control defines an authorisation control paradigm based on policies. ABAC serves to control fine-grained authorisation by combining the characteristics of users, resources and the environment, efficiently and dynamically managing all your organisation's privileges, in real time.
The policies provide a user-friendly way of establishing which characteristics a user must fulfil to be allowed to perform a particular action with regard to a defined resource perimeter.
Zero Trust: Two-level engine
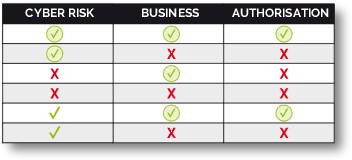
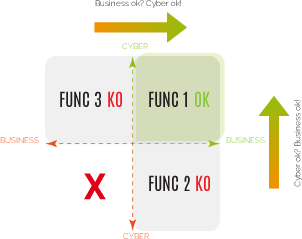
BST has the capacity to establish two levels of control over the authorisation model of an application, making it possible for a team, typically CISO, Control, Regulator… to establish controls over critical profiling elements, while the business owner can then manage greater levels of segregation for them in real time, improving experience and Time to Market, without the CISO department losing overall control of the critical part of the model.
- Profiling level 1: typically controlled by the cybersecurity department. It allows them to limit the capacities that any user may have within a specific application.
- Profiling level 2: typically assigned by the business owner, these are the capacities defined for a user within the limits established by the perimeter assigned at level 1.
For example:
Level 1: CISO enables a team to view all information for a continent, such as Europe.
Level 2: The business manager enables this team to view information for Spain and France, excluding the other European countries authorised by level 1.
2 security layers
Authorisation Services
- ABAC engine
- Policies
- Execution in real time
- User-friendly
- Traceable and auditable